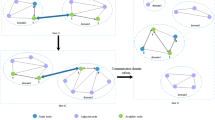
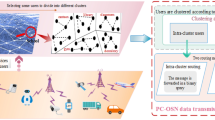
Abstract
Effective data transmission is a key technology in researching opportunistic networks. Increased data packet transmission among nodes can easily cause the death of nodes, especially in social networks environment. However, effective packet transmission is seldom discussed in existing algorithms in opportunistic networks research. In this study, an efficient data packet iteration and transmission (EDPIT) algorithm, which selects data packets via iteration, is proposed to save energy and overhead during transmission. The effective transmission among nodes in this algorithm improves the transmission rate of data packets. With satisfactory results from simulation and comparison with some existing algorithms, the EDPIT algorithm is found to not only reduce energy consumption but also improve the delivery ratio and overhead in opportunistic social networks.









Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Availability of data and materials
Data sharing not applicable to this article as no datasets were generated or analyzed during the current study.
References
Calabrese M, Amato A, Lecce VD et al (2010) Hierarchical-granularity holonic modelling. J Ambient Intell Hum Comput 1(3):199–209. https://doi.org/10.1007/s12652-010-0013-3
Cheng H, Sun F, Buthpitiya S, Griss M (2012) SensOrchestra: collaborative sensing for symbolic location recognition. Mob Comput Appl Serv 76:195–210. https://doi.org/10.1007/978-3-642-29336-8_11
Cheong M, Lee VCS (2018) A microblogging-based approach to terrorism informatics: exploration and chronicling civilian sentiment and response to terrorism events via Twitter. Inf Syst Front 13(13):45–59. https://doi.org/10.1007/s10796-010-9273-x
Guan P, Wu J (2019) Effective data communication based on social community in social opportunistic networks. IEEE Access 7(1):12405–12414. https://doi.org/10.1109/ACCESS.2019.2893308
Han B, Pan H, Kumar A (2012) Mobile data offloading through opportunistic communications and social participation. IEEE Trans Mob Comput 11(5):821–834. https://doi.org/10.1109/tmc.2011.101
Jaroucheh Z (2011) Recognize contextual situation in pervasive environments using process miningtechniques. J Ambient Intell Hum Comput 2(1):53–69. https://doi.org/10.1007/s12652-010-0038-7
Koukoumidis E, Peh L, SignalGuru Martonosi M (2011) Leveraging mobile phones for collaborative traffic signal schedule advisory. Proc ACM MobiSys 2011:27–140. https://doi.org/10.1145/1999995.2000008
Lin Y, Wang X, Zhang L et al (2015) The impact of node velocity diversity on mobile opportunistic network performance. J Netw Comput Appl 55:47–58. https://doi.org/10.1016/j.jnca.2015.04.010
Lin Y, Wang X, Hao F et al (2018) An on-demand coverage based self-deployment algorithm for big data perception in mobile sensing networks. Future Gen Comput Syst 82:220–234. https://doi.org/10.1016/j.future.2018.01.007
Lin Y, Cai Z, Wang X, Hao F (2019) Incentive mechanisms for crowdblocking rumors in mobile social networks. IEEE Trans Vehicular Technol 1:1–17. https://doi.org/10.1109/TVT.2019.2930667
Mayer JM, Hiltz SR, Barkhuus L et al (2016) Supporting opportunities for context-aware social matching: an experience sampling. In: Study. conference on human factors in computing systems. ACM. https://doi.org/10.1145/2858036.2858175
Nguyen P, Nahrstedt K (2016) Context-aware crowd-sensing in opportunistic mobile social networks. In: IEEE, international conference on mobile ad hoc and sensor systems. IEEE, pp 477–478. https://doi.org/10.1109/MASS.2015.80
Ra M, Liu B, Porta T, Medusa GR (2012) A programming framework for crowd-sensing applications. Proc ACM MobiSys 2012:337–350. https://doi.org/10.1145/2307636.2307668
Ristanovic N, Theodorakopoulos G, Le Boudec JY (2012) Traps and pitfalls of using contact traces in performance studies of opportunistic networks. NFOCOM, 2012 Proceedings IEEE. Ieee, pp 1377–1385. https://doi.org/10.1109/INFCOM.2012.6195502
Shih Y-Y, Chung W-H, Chiu A-C, Wei H-Y (2017) Enabling low-latency applications in fog-radio access network. IEEE Netw 31(1):52–58. https://doi.org/10.1109/MNET.2016.1500279NM
Talipov E, Chon Y, Cha H (2015) User context-based data delivery in opportunistic smartphone networks. Pervasive Mob Comput 17:122–138. https://doi.org/10.1016/j.pmcj.2014.06.001
Toledano E, Sawaday D, Lippman A, Holtzman H, Casalegno F (2013) CoCam: a collaborative content sharing framework based on opportunistic P2P networking. Proc IEEE CCNC 2013:158–163. https://doi.org/10.1109/CCNC.2013.6488440
Trifunovic S, Kurant M, Hummel KA et al (2014) Preventing spam in opportunistic networks. Comput Commun 41:31–42. https://doi.org/10.1016/j.comcom.2013.12.003
Wang G, Wang B, Gao Y (2010) Dynamic spray and wait routing algorithm with quality of node in delay tolerant network. In: Proceedings of the IEEE international conference on communications and mobile computing (CMC), vol 3, pp 452–456. https://doi.org/10.1109/CMC.2010.83
Wang X, Lin Y, Zhao Y (2018a) A novel approach for inhibiting misinformation propagation in human mobile opportunistic networks. Peer-to-Peer Netw Appl 10(2):377–394. https://doi.org/10.1007/s12083-016-0438-3
Wang R, Wang X, Hao F et al (2018b) Social identity- aware opportunistic routing in mobile social networks. Trans Emerg Telecommun Technol 8:1–12. https://doi.org/10.1002/ett.3297
Wu J, Chen Z (2016) Reducing energy consumption and overhead based on mobile health in big data opportunistic networks. Wirel Pers Commun 92(4):1365–1385. https://doi.org/10.1007/s11277-016-3610-4
Wu J, Chen Z (2017) Human activity optimal cooperation objects selection routing scheme in opportunistic networks communication. Wirel Pers Commun 95(3):3357–3375. https://doi.org/10.1007/s11277-017-4001-1
Wu J, Chen Z (2018) Sensor communication area and node extend routing algorithm in opportunistic networks. Peer-to-Peer Netw Appl 11:90–100. https://doi.org/10.1007/s12083-016-0526-4
Wu XH, Gu XF, Poslad S (2016) Routing algorithm based on social relations in opportunistic networks. In: International computer conference on wavelet active media technology and information processing. IEEE, pp 146–149. https://doi.org/10.1109/ICCWAMTIP.2015.7493963
Wu J, Chen J, Zhao M (2017) Effective information transmission based on socialization nodes in opportunistic networks. Comput Netw 129(part 1):297–305. https://doi.org/10.1016/j.comnet.2017.10.005
Wu J, Chen Z, Zhao M (2018a) SECM: status estimation and cache management algorithm in opportunistic networks. J Supercomput 1:1–12. https://doi.org/10.1007/s11227-018-2675-0
Wu J, Chen Z, Zhao M (2018b) Weight distribution and community reconstitution based on communities communications in social opportunistic networks. Peer-to-Peer Netw Appl. https://doi.org/10.1007/s12083-018-0649-x
Wu J, Chen Z, Zhao M (2019a) Information cache management and data transmission algorithm in opportunistic social networks. Wirel Netw 25(6):2977–2988. https://doi.org/10.1007/s11276-018-1691-6
Wu J, Tian X, Tan Y (2019b) Hospital evaluation mechanism based on mobile health for IoT system in social networks. Comput Biol Med 109:138–147. https://doi.org/10.1016/j.compbiomed.2019.04.021
Wu J, Yu G, Guan P (2019c) Interest characteristic probability predicted method in social opportunistic networks. IEEE Access 7(1):59002–59012. https://doi.org/10.1109/ACCESS.2019.2915359
Wu J, Guan P, Tan Y (2019d) Diagnosis and data probability decision based on Non-small cell lung cancer in medical system. IEEE Access 7(1):44851–44861. https://doi.org/10.1109/ACCESS.2019.2909538
Yuan P, Wang W, Wang C (2015) Poster: an adaptive copy spraying scheme for data forwarding in mobile opportunistic networks. In: Proceedings of the 16th ACM international symposium on mobile ad hoc networking and computing. ACM, pp 377–378. https://doi.org/10.1145/2746285.2764862
Zhao D, Ma H, Tang S et al (2015) COUPON: a cooperative framework for building sensing maps in mobile opportunistic networks. IEEE Trans Parallel Distrib Syst 26(2):392–402. https://doi.org/10.1109/tpds.2014.2308178
Funding
This work was supported in The National Natural Science Foundation of China (61672540);Hunan Provincial Natural Science Foundation of China (2018JJ3299, 2018JJ3682); ChinaPostdoctoral Science Foundation funded project (2017M612586); Foundation of Central SouthUniversity (185684); Major Program of National Natural Science Foundation of China (71633006).
Author information
Authors and Affiliations
Contributions
JW, ZC and MZ designed the project and drafted the manuscript, collected the data, wrote the code and performed the analysis. All participated in finalizing and approved the manuscript.
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no competing interests (all financial).
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Wu, J., Chen, Z. & Zhao, M. An efficient data packet iteration and transmission algorithm in opportunistic social networks. J Ambient Intell Human Comput 11, 3141–3153 (2020). https://doi.org/10.1007/s12652-019-01480-2
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12652-019-01480-2