Abstract
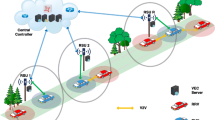
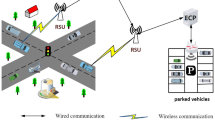
Mobile Edge Computing (MEC) is a promising solution to improve vehicular services through offloading computation to cloud servers in close proximity to mobile vehicles. However, the self-interested nature together with the high mobility characteristic of the vehicles make the design of the computation offloading scheme a significant challenge. In this paper, we propose a new Vehicular Edge Computing (VEC) framework to model the computation offloading process of the mobile vehicles running on a bidirectional road. Based on this framework, we adopt a contract theoretic approach to design optimal offloading strategies for the VEC service provider, which maximize the revenue of the provider while enhancing the utilities of the vehicles. To further improve the utilization of the computing resources of the VEC servers, we incorporate task priority distinction as well as additional resource providing into the design of the offloading scheme, and propose an efficient VEC server selection and computing resource allocation algorithm. Numerical results indicate that our proposed schemes greatly enhance the revenue of the VEC provider, and concurrently improve the utilization of cloud computing resources.





Similar content being viewed by others
References
Qu Z, Keeney J, Robitzsch S, Zaman F, Wang X (2016) Multilevel pattern mining architecture for automatic network monitoring in heterogeneous wireless communication networks. China Commun 13(7):108–116
Zhou Z, Wang Y, Wu QMJ, Yang C, Sun X (2017) Effective and efficient global context verification for image copy detection. IEEE Trans Inf Forensics Secur 12(1):48–63
Li J, Li X, Yang B, Sun X (2015) Segmentation-based image copy-move forgery detection scheme. IEEE Trans Inf Forensics Secur 10(3):507–518
Chen X, Chen S, Wu Y (2017) Coverless information hiding method based on the chinese character encoding. J Internet Technol 18(2):91–98
Fu Z, Ren K, Shu J, Sun X, Huang F (2016) Enabling personalized search over encrypted outsourced data with efficiency improvement. IEEE Trans Parallel Distrib Syst 27(9):2546–2559
Fu Z, Wu X, Guan C, Sun X, Ren K (2016) Toward efficient multi-keyword fuzzy search over encrypted outsourced data with accuracy improvement. IEEE Trans Inf Forensics Secur 11(12):2706–2716
Kong Y, Zhang M, Ye D (2017) A belief propagation-based method for task allocation in open and dynamic cloud environments. Knowl-Based Syst 115:123–132
Shen J, Shen J, Chen X, Huang X, Susilo W An efficient public auditing protocol with novel dynamic structure for cloud data. IEEE Trans Information Forensics and Security, accepted
Liu Q, Cai W, Shen J, Fu Z, Liu X, Linge N (2016) A speculative approach to spatial-temporal efficiency with multi-objective optimization in a heterogeneous cloud environment. Secur Commun Netw 9(17):4002–4012
Liu X, Li Y, Chen H (2016) Wireless resource scheduling based on backoff for multiuser multiservice mobile cloud computing. IEEE Trans Veh Technol 65(11):9247–9259
Shen J, Chang S, Shen J, Liu Q, Sun X (2016) A lightweight multi-layer authentication protocol for wireless body area networks. Future Generation Computer Systems
Gu B, Sheng VS A robust regularization path algorithm for ν-support vector classification. IEEE Trans Neural Networks and Learning Systems, accepted
Zhang K, Mao Y, Leng S, Zhao Q, Li L, Peng X, Pan L, Zhang G, Maharjan S, Zhang Y (2016) Energy-efficient offloading for mobile edge computing in 5G heterogenous networks. IEEE Access 4:5896–5907
Yu R, Huang X, Kang J, Ding J, Maharjan S, Gjessing S, Zhang Y (2015) Cooperative resource management in cloud-enabled vehicular networks. IEEE Trans Ind Electron 62(12):7938–7951
Werin L, Wijkander H (1992) Contract economics. Blackwell, Oxford
Huang X, Yu R, Kang J, Wang N, Maharjan S, Zhang Y (2016) Software defined networking with pseudonym systems for secure vehicular clouds. IEEE Access 4:3522–3534
Xia Z, Wang X, Sun X, Wang Q (2016) A secure and dynamic multi-keyword ranked search scheme over encrypted cloud data. IEEE Trans Parallel Distrib Syst 27(2):340–352
Xia Z, Wang X, Zhang L, Qin Z, Sun X, Ren K (2016) A privacy-preserving and copy-deterrence content-based image retrieval scheme in cloud computing. IEEE Trans Inf Forensics Secur 11(11):2594–2608
Zheng K, Meng H, Chatzimisios P, Lei L, Shen X (2015) An SMDP-based resource allocation in vehicular cloud computing systems. IEEE Trans Ind Electron 62(12):7920–7928
Kwak D, Liu R, Kim D, Nath B, Iftode L (2016) Seeing is believing: sharing real-time visual traffic information via vehicular clouds. IEEE Access 4:3617–3631
Pan Z, Jin P, Lei J, Zhang Y, Sun X, Kwong S (2016) Fast reference frame selection based on content similarity for low complexity HEVC encoder. J Vis Commun Image Represent 40(Part B):516–524
Chen Y, Hao C, Wu W, Wu E (2016) Robust dense reconstruction by range merging based on confidence estimation. Sci China Inf Sci 59(9):1–11
Yuan C, Xia Z, Sun X (2017) Coverless image steganography based on SIFT and BOF. J Internet Technol 18(2):209–216
Tong L, Li Y, Gao W (2016) A hierarchical edge cloud architecture for mobile computing. In: Proceedings of the IEEE international conference on computer communications (INFOCOM), pp 1–9
Wang Y, Sheng M, Wang X, Wang L, Li J (2016) Mobile-edge computing: partial computation offloading using dynamic voltage scaling. IEEE Trans Commun 64(10):4268–4282
Sun X, Ansari N (2016) PRIMAL: profit maximization avatar placement for mobile edge computing. In: Proceedings of IEEE international conference on communications (ICC), pp 1–6
Sapienza M, Torre GL, Leombruno G, Guardo E, Cavallo M, Tomarchio O (2016) Solving critical events through mobile edge computing: an approach for smart cities. In: Proceedings of IEEE international conference on smart computing (SMARTCOMP), pp 1–5
Kumar N, Zeadally S, Rodrigues JJPC (2016) Vehicular delay-tolerant networks for smart grid data management using mobile edge computing. IEEE Commun Mag 54(10):60–66
Chen X, Jiao L, Li W, Fu X (2016) Efficient multi-user computation offloading for mobile-edge cloud computing. IEEE/ACM Trans Netw 24(5):2795–2808
Gao L, Wang X, Xu Y, Zhang Q (2011) Spectrum trading in cognitive radio networks: a contract-theoretic modeling approach. IEEE J Sel Areas Commun 29(4):843–855
Li Y, Wang P, Niyato D, Zhang Y (2014) Contract-theoretic modeling for content delivery in relay-based publish-subscribe networks. In: IEEE international conference on communications (ICC), pp 2678–2683
Zhang Y, Song L, Saad W, Dawy Z, Han Z (2015) Contract-based incentive mechanisms for device-to-device communications in cellular networks. IEEE J Sel Areas Commun 33(10):2144–2155
Zhang K, Mao Y, Leng S, Maharjan S, Zhang Y, Vinel A, Jonsson M (2016) Incentive-driven energy trading in the smart grid. IEEE Access 4:1243–1257
Yuan C, Sun X, LV R (2016) Fingerprint liveness detection based on multi-scale LPQ and PCA. China Commun 13(7):60–65
Zhang Y, Yu R, Yao W, Xie S, Xiao Y, Guizani M (2011) Home M2M networks: architectures, standards, and QoS improvement. IEEE Commun Mag 49(4):44–52
Fu Z, Huang F, Sun X, Vasilakos AV, Yang C Enabling semantic search based on conceptual graphs over encrypted outsourced data. IEEE Trans Services Computing, accepted
Pan Z, Lei J, Zhang Y, Sun X, Kwong S (2016) Fast motion estimation based on content property for low-complexity H.265/HEVC encoder. IEEE Trans Broadcast 62(3):675–684
Gu B, Sun X, Sheng VS Structural minimax probability machine. IEEE Trans Neural Networks and Learning Systems, accepted
Pan Z, Zhang Y, Kwong S (2015) Efficient motion and disparity estimation optimization for low complexity multiview video coding. IEEE Trans Broadcast 61(2):166–176
Zhou Z, Yang C, Chen B, Sun X, Liu Q, Wu QMJ (2016) Effective and efficient image copy detection with resistance to arbitrary rotation. IEICE Trans. Inf Syst E99-D(6):1531–1540
Fu Z, Huang F, Ren K, Weng J, Wang C (2017) Privacy-preserving smart semantic search based on conceptual graphs over encrypted outsourced data. IEEE Trans Inf Forensics Secur 12(8):1874– 1884
Tian Q, Chen S (2017) Cross-heterogeneous-database age estimation through correlation representation learning. Neurocomputing 238:286–295
Bolton P, Dewatripont M (2005) Contract theory. MIT Press, Cambridge, pp 31–64
Zhang Y, Sun X, Wang B (2016) Efficient algorithm for K-barrier coverage based on integer linear programming. China Commun 13(7):16–23
Gu B, Sheng VS, Tay KY, Romano W, Li S (2015) Incremental support vector learning for ordinal regression. IEEE Trans Neural Netw Learn Syst 26(7):1403–1416
Acknowledgments
This work is in part supported by the National Natural Science Foundation of China under Grant No.61374189, the joint fund of the Ministry of Education of P.R. China and China Mobile under Grant MCM20160304.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Zhang, K., Mao, Y., Leng, S. et al. Contract-theoretic Approach for Delay Constrained Offloading in Vehicular Edge Computing Networks. Mobile Netw Appl 24, 1003–1014 (2019). https://doi.org/10.1007/s11036-018-1032-0
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11036-018-1032-0