Abstract
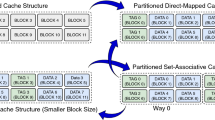
Side channel cryptanalysis has received significant attention lately, because it provides a low-cost and facile way to reveal the secret information held on a secure computing system. One particular type of side channel attacks, called cache-based side channel attacks, aims to deduce information about the state of a cryptographic algorithm or its key by observing the data-dependent behavior of a microprocessor’s cache memory. These attacks have been proven successful and very hard to protect against. In this paper, we introduce the use of the Cache Decay approach as an aid to guard against cache-based side channel attacks. Cache Decay controls the lifetime (called decay interval) of the cache items and was initially proposed for cache power leakage savings. By randomly selecting the decay interval of the cache, we actually create caches with non-deterministic behavior in regard to their statistics. Thus, as we demonstrate, multiple runs of the same algorithm (performing on the same input) will result in different cache statistics, defending against the attacker and reinforcing the protection offered by the system. In our work, we use a cycle-based processor simulator, enhanced with the required modifications, in order to evaluate our proposal and show that our technique can be used effectively to protect against cache-based side channel attacks.
Similar content being viewed by others
References
Bernstein DJ. Cache-timing attacks on AES. http://cr.yp.to/antiforgery/cachetiming-20050414.pdf
Osvik DA, Shamir A, Tromer E (2005) Cache attacks and countermeasures: the case of AES. Cryptology ePrint Archive, Report 2005/271
Persival C. Cache missing for fun and profit. http://daemonology.net/papers/htt.pdf
Goldreich O, Ostrovsky R (1996) Software protection and simulation on oblivious RAMs. J ACM 43(3):431–473
Zhuang X, Zhang T, Lee H-HS, Pande S (2004) Hardware assisted control flow obfuscation for embedded processors. In: Proceedings of international conference on compilers architectures and synthesis for embedded systems, pp 292–302
Zhuang X, Zhang T, Pande S (2004) HIDE: an infrastructure for efficiently protecting information leakage on the address bus. In: Proceedings of architectural support for programming languages and operating systems, pp 82–84
Oswald E, Mangard S, Pramstaller N, Rijmen V (2005) A side-channel analysis resistant description of the AES S-box. In: Proceedings FSE 2005. Lecture notes in computer science, vol 3557. Springer, Berlin, pp 413–423
Kocher PC (1996) Timing attacks on implementations of Diffie-Hellman, RSA, DSS, and other systems. In: CRYPTO’96: proceedings of the 16th annual international cryptology conference on advances in cryptology. Lecture notes in computer science, vol 1109. Springer, Berlin, pp 104–113
Kocher PC, Jaffe J, Jun B (1999) Differential power analysis. In: CRYPTO’99: proceedings of the 19th annual international cryptology conference on advances in cryptology. Lecture notes in computer science, vol 1666. Springer, Berlin, pp 388–397
Boneh D, DeMillo R, Lipton R (2001) On the importance of checking cryptographic protocols for faults. J Cryptol 14(2):101–119
Bao F, Deng RH, Han Y, Jeng AB, Narasimhalu AD, Ngair T-H (1998) Breaking public key cryptosystems on tamper resistant devices in the presence of transient faults. In: Christianson B, Crispo B, Lomas TM, Roe MR (eds) Proceedings of the 5th international workshop on security protocols. Lecture notes in computer science, vol 1361. Springer, Berlin, pp 115–124
Kaxiras S, Hu Z, Martonosi M (2001) Cache decay: exploiting generational behavior to reduce cache leakage power. In: Proceedings of the 28th annual international symposium on computer architecture ISCA, June 2001, pp 240–251
Kaxiras S, Xekalakis P, Keramidas G (2005) A simple mechanism to adapt leakage-control policies to temperature. In: Proceedings of 2005 international symposium on low power electronics and design, pp 54–59
Hu Z, Kaxiras S, Martonosi M (2002) Timekeeping in the memory system: predicting and optimizing memory behavior. In: Proceedings of the 29th annual international symposium on computer architecture (ISCA), Anchorage, Alaska, May 2002, pp 209–220
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Keramidas, G., Antonopoulos, A., Serpanos, D.N. et al. Non deterministic caches: a simple and effective defense against side channel attacks. Des Autom Embed Syst 12, 221–230 (2008). https://doi.org/10.1007/s10617-008-9018-y
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10617-008-9018-y