Apple Platform Deployment
- Welcome
- Intro to Apple platform deployment
- What’s new
-
-
- Accessibility payload settings
- Active Directory Certificate payload settings
- AirPlay payload settings
- AirPlay Security payload settings
- AirPrint payload settings
- App Lock payload settings
- Associated Domains payload settings
- Automated Certificate Management Environment (ACME) payload settings
- Autonomous Single App Mode payload settings
- Calendar payload settings
- Mobile payload settings
- Mobile Private Network payload settings
- Certificate Preference payload settings
- Certificate Revocation payload settings
- Certificate Transparency payload settings
- Certificates payload settings
- Conference Room Display payload settings
- Contacts payload settings
- Content Caching payload settings
- Directory Service payload settings
- DNS Proxy payload settings
- DNS Settings payload settings
- Fonts payload settings
- Domains payload settings
- Energy Saver payload settings
- Exchange ActiveSync (EAS) payload settings
- Exchange Web Services (EWS) payload settings
- Extensible Single Sign-on payload settings
- Extensible Single Sign-on Kerberos payload settings
- Extensions payload settings
- FileVault payload settings
- Finder payload settings
- Firewall payload settings
- Fonts payload settings
- Global HTTP Proxy payload settings
- Google Accounts payload settings
- Home Screen Layout payload settings
- Identification payload settings
- Identity Preference payload settings
- Kernel Extension Policy payload settings
- LDAP payload settings
- Lights Out Management payload settings
- Lock Screen Message payload settings
- Login Window payload settings
- Managed Login Items payload settings
- Mail payload settings
- Network Usage Rules payload settings
- Notifications payload settings
- Parental Controls payload settings
- Passcode payload settings
- Printing payload settings
- Privacy Preferences Policy Control payload settings
- Relay payload settings
- SCEP payload settings
- Security payload settings
- Setup Assistant payload settings
- Single Sign-on payload settings
- Smart Card payload settings
- Subscribed Calendars payload settings
- System Extensions payload settings
- System Migration payload settings
- Time Machine payload specifics
- TV Remote payload settings
- Web Clips payload settings
- Web Content Filter payload settings
- LDAP payload settings
-
- Declarative app configuration
- Authentication credentials and identity asset declaration
- Background task management declarative
- Calendar declarative configuration
- Certificates declarative configuration
- Contacts declarative configuration
- Exchange declarative configuration
- Google Accounts declarative configuration
- LDAP declarative configuration
- Legacy interactive profile declarative configuration
- Legacy profile declarative configuration
- Mail declarative configuration
- Maths and Calculator app declarative configuration
- Passcode declarative configuration
- Passkey Attestation declarative configuration
- Safari extensions management declarative configuration
- Screen Sharing declarative configuration
- Service configuration files declarative configuration
- Software Update declarative configuration
- Software Update settings declarative configuration
- Storage management declarative configuration
- Subscribed Calendars declarative configuration
- Glossary
- Document revision history
- Copyright

Configure devices to work with APNs
Mobile device management (MDM) solutions use the Apple Push Notification service (APNs) to maintain persistent communication with Apple devices across both public and private networks. Using APNs, Apple devices learn about updates, MDM policies and incoming messages. MDM solutions require multiple certificates, including an APNs certificate to talk to devices, an SSL certificate to communicate securely, and a certificate to sign configuration profiles.
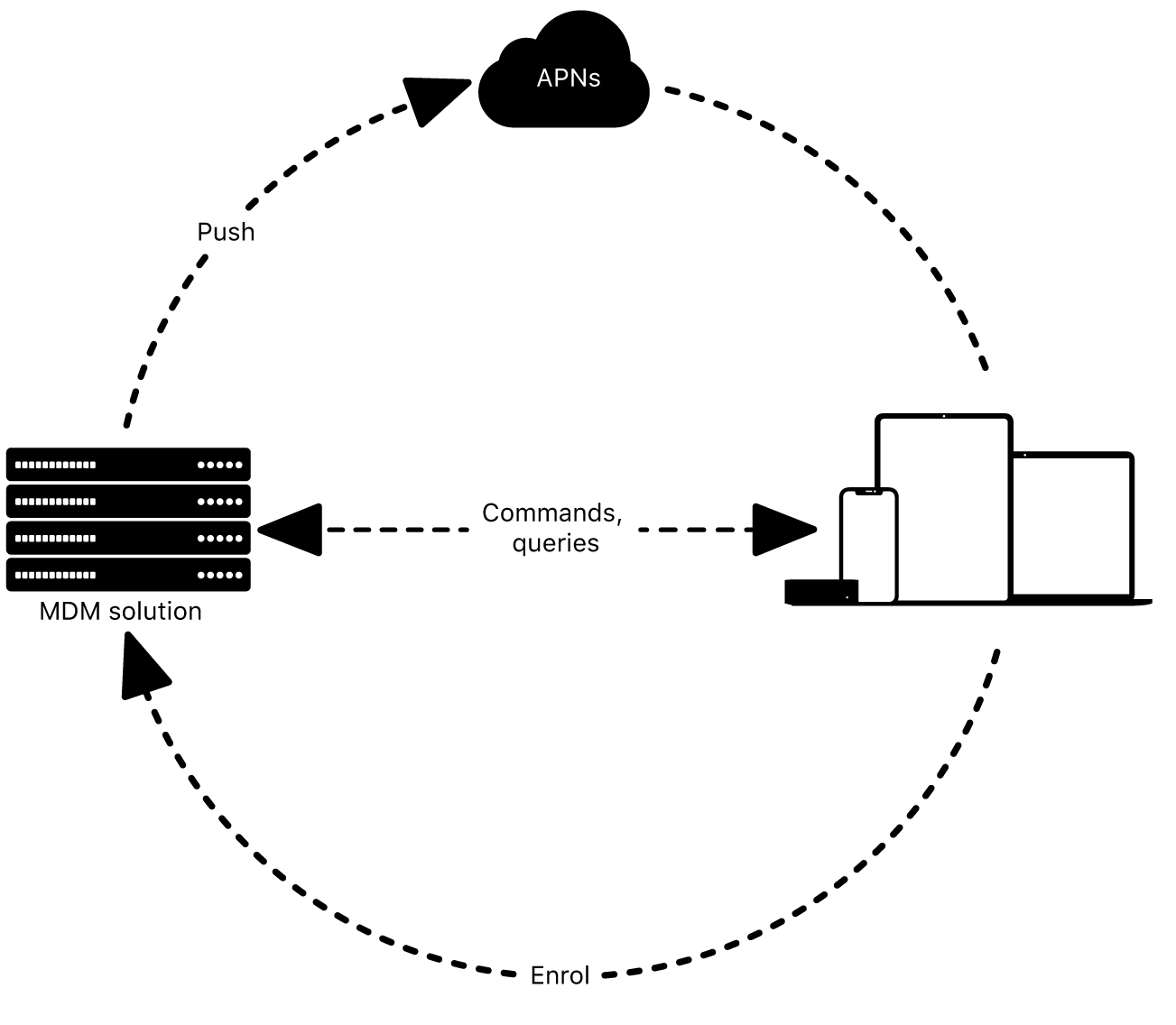
For your Apple devices to work with APNs, allow network traffic from the devices to the Apple network (17.0.0.0/8) directly or by using a network proxy. Apple devices must be able to connect to specific ports on specific hosts:
TCP port 443 during device activation, and afterwards for fallback if devices can’t reach APNs on port 5223
TCP port 5223 to communicate with APNs
TCP port 443 or 2197 to send notifications from MDM to APNs
You may also need to configure your web proxy or firewall ports to allow all network traffic from Apple devices to the Apple network. In iOS 13.4, iPadOS 13.4, macOS 10.15.4 and tvOS 13.4, or later, APNs can use a web proxy when it’s specified in a proxy auto-config (PAC) file.
Multiple layers of security are applied to APNs at the endpoints and the servers. Attempts to inspect the traffic or reroute it result in the client, APNs and the push provider servers marking the network conversation as compromised and invalid. No confidential or proprietary information is transmitted through APNs.
Tip: When you create APNs certificates for use with MDM, note the Managed Apple Account (recommended) or Apple Account you use — you’ll need it when it’s time to renew the certificates, which you must do annually. Also, be prepared to update all certificates used by your MDM solution well before they expire. For more information, see the Apple Push Certificates Portal.
