
User Enrolment and MDM
User Enrolment is designed for BYOD — or bring-your-own-device deployments — where the user, not the organisation, owns the device. It works with an identity provider (IdP), Google Workspace or Microsoft Entra ID, and Apple School Manager or Apple Business Manager and a third-party MDM solution. It also works with device management in Apple Business Essentials.
The four stages of User Enrolment into MDM are:
Service discovery: The device identifies itself to the MDM solution.
User enrolment: The user provides credentials to an identity provider (IdP) for authorisation to enrol in the MDM solution.
Session token: A session token is issued to the device to allow ongoing authentication.
MDM enrolment: The enrolment profile is sent to the device with payloads configured by the MDM administrator.
User Enrolment and Managed Apple Accounts
User Enrolment requires Managed Apple Accounts. These are owned and managed by an organisation and provide employees access to certain Apple services. In addition, Managed Apple Accounts:
Are created manually, or automatically using federated authentication
Are integrated with a Student Information System (SIS) or uploading .csv files (Apple School Manager only)
Can also be used to sign in with an assigned role in Apple School Manager, Apple Business Manager or Apple Business Essentials
When a user removes an enrolment profile, all configuration profiles, their settings and Managed Apps based on that enrolment profile are removed with it.
User Enrolment is integrated with Managed Apple Accounts to establish a user identity on the device. The user must successfully authenticate for enrolment to be completed. The Managed Apple Account can be used alongside the personal Apple Account that the user has already signed in with; the two don’t interact with each other.
User Enrolment and federated authentication
Although Managed Apple Accounts can be created manually, organisations can take advantage of synchronisation with an IdP, Google Workspace or Microsoft Entra ID and User Enrolment. To do so, your organisation must first:
Manage user credentials with an IdP, Google Workspace or Microsoft Entra ID
If you have an on-premise version of Active Directory, additional configuration must be taken to prepare for federated authentication.
Sign up your organisation in Apple School Manager, Apple Business Manager or Apple Business Essentials
Set up federated authentication in Apple School Manager, Apple Business Manager or Apple Business Essentials
Configure an MDM solution and link it to Apple School Manager, Apple Business Manager or Apple Business Essentials, or use the device management that’s built right in to Apple Business Essentials
(Optional) Create Managed Apple Accounts
User Enrolment and Managed Apps (macOS)
User Enrolment has added Managed Apps to macOS (this feature was already possible with Device Enrolment and Automated Device Enrolment). Managed Apps that use CloudKit use the Managed Apple Account associated with the MDM enrolment. MDM administrators must add the InstallAsManaged key to the InstallApplication command. Like iOS and iPadOS apps, these apps can be automatically removed when a user unenrols from MDM.
User Enrolment and per-app networking
In iOS 16, iPadOS 16.1 and visionOS 1.1, or later, per-app networking is available for VPN (known as per-app VPN), DNS proxies and web content filters for devices enrolled with User Enrolment. This means that only network traffic initiated by Managed Apps is passed through the DNS proxy, the web content filter or both. A user’s personal traffic stays separated and won’t be filtered or proxied by an organisation. This is accomplished using new key-value pairs for the following payloads:
How users enrol their personal devices
In iOS 15, iPadOS 15, macOS 14 and visionOS 1.1, or later, organisations can use a streamlined User Enrolment process, built directly into the Settings app to make it easier for users to enrol their personal devices.
To do this:
On iPhone, iPad and Apple Vision Pro, the user navigates to Settings > General > VPN & Device Management and then selects the Sign In to Work or School Account button.
On Mac, the user navigates to Settings > Privacy & Security > Profiles and then selects the Sign In to Work or School Account button.
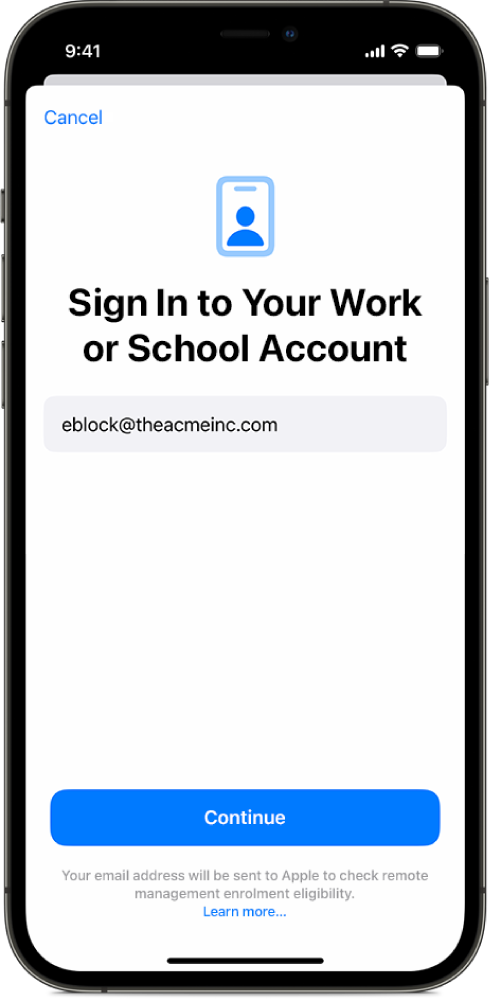
When they enter their Managed Apple Account, service discovery identifies the MDM solution’s enrolment URL.
The user then enters their organisation username and password. After the organisation’s authentication succeeds, the enrolment profile is sent to the device. A session token is also issued to the device to allow ongoing authorisation. The device then begins the enrolment process, and prompts the user to sign in with their Managed Apple Account. On iPhone, iPad and Apple Vision Pro, the authentication process can be streamlined by using enrolment single sign-on to reduce repeated authentication prompts.
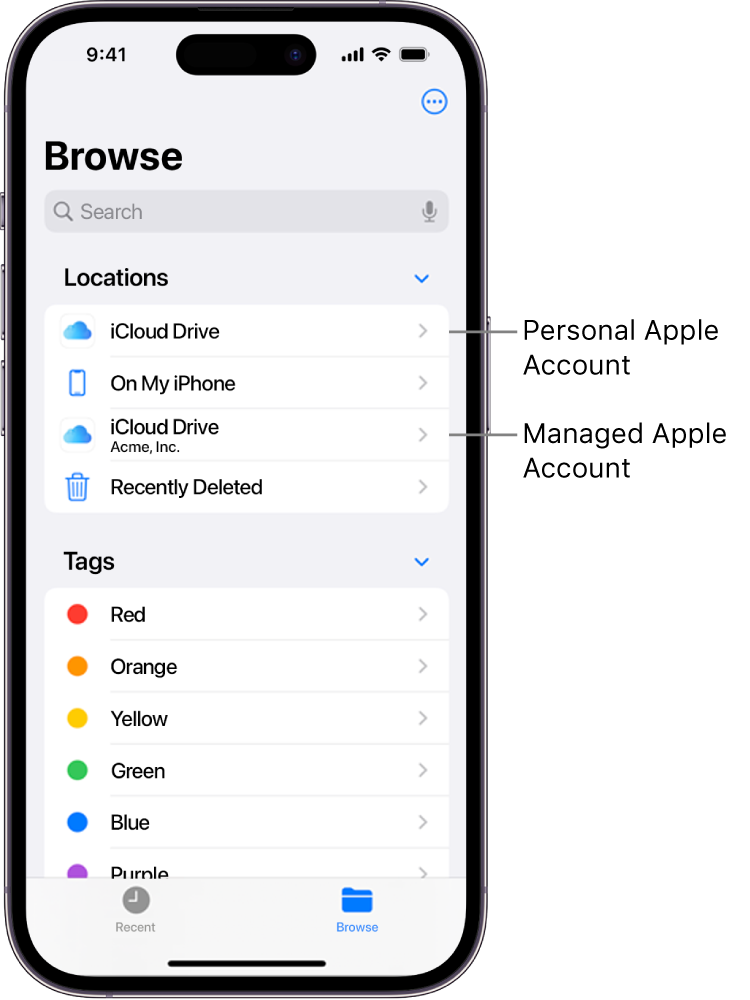
When enrolment is complete, the new managed account is displayed prominently within the Settings app (iPhone, iPad and Apple Vision Pro) and System Settings (Mac). This allows users to still access files in their personal Apple Account–created iCloud Drive. The iCloud Drive for the organisation (associated with the user’s Managed Apple Account) appears separately in the Files app.
On iPhone, iPad and Apple Vision Pro, Managed Apps and managed web-based documents all have access to the organisation’s iCloud Drive, and the MDM administrator can help keep specific personal and organisational documents separate by using specific restrictions. For more information, see Managed App restrictions and capabilities.
Users can see details about what is being managed on their personal device and how much iCloud storage space is provided by their organisation. Because the user owns the device, User Enrolment can apply only a limited set of payloads and restrictions to it. For more information, see User Enrolment MDM information.
How Apple separates user data from organisation data
When User Enrolment is complete, separate encryption keys are automatically created on the device. If the device gets unenrolled by the user or remotely using MDM, those encryption keys are securely destroyed. The keys are being used to cryptographically separate the managed data listed below:
App data containers: iPhone, iPad, Mac and Apple Vision Pro
Calendar: iPhone, iPad, Mac and Apple Vision Pro
Devices must be using iOS 16, iPadOS 16.1, macOS 13 and visionOS 1.1, or later.
Keychain items: iPhone, iPad, Mac and Apple Vision Pro
Note: The third-party Mac app must use the data protection keychain API. For more information, see the Apple Developer documentation kSecUseDataProtectionKeychain.
Mail attachments and body of the mail message: iPhone, iPad, Mac and Apple Vision Pro
Notes: iPhone, iPad, Mac and Apple Vision Pro
Reminders: iPhone, iPad, Mac and Apple Vision Pro
Devices must be using iOS 17, iPadOS 17, macOS 14 and visionOS 1.1, or later.
If a user is signed in with a personal Apple Account and Managed Apple Account, Sign in with Apple automatically uses the Managed Apple Account for Managed Apps and the personal Apple Account for unmanaged apps. When using a sign-in flow in Safari or SafariWebView within a managed app, the user can select and enter their Managed Apple Account to associate the sign-in with their work account.
System administrators can manage only an organisation’s accounts, settings and information provisioned with MDM, never a user’s personal account. In fact, the same features that keep data secure in organisation-owned Managed Apps also protect a user’s personal content from entering the corporate data stream.
MDM can | MDM can’t |
|---|---|
Configure accounts | See personal information, usage data or logs |
Access inventory of Managed Apps | Access inventory of personal apps |
Remove managed data only | Remove any personal data |
Install and configure apps | Take over management of a personal app |
Require a passcode | Require a complex passcode or password |
Enforce certain restrictions | Access device location |
Configure per-app VPN | Access unique device identifiers |
| Remotely wipe the entire device |
| Manage Activation Lock |
| Access roaming status |
| Turn on Lost Mode |
Note: For iPhone and iPad, administrators can require passcodes with a minimum of six characters and prevent users from using simple passcodes (for example, “123456” or “abcdef”) but can’t require complex characters or passwords.
