
Integrate Mac computers with Active Directory
You can configure a Mac to access basic user account information in a Active Directory domain of a Windows 2000 (or later) server. The Active Directory connector is listed in the Services pane of Directory Utility, and it generates all attributes required for macOS authentication from standard attributes in Active Directory user accounts. The connector also supports Active Directory authentication policies, including password changes, expirations, forced changes, and security options. Because the connector supports these features, you don’t need to make schema changes to the Active Directory domain to get basic user account information.
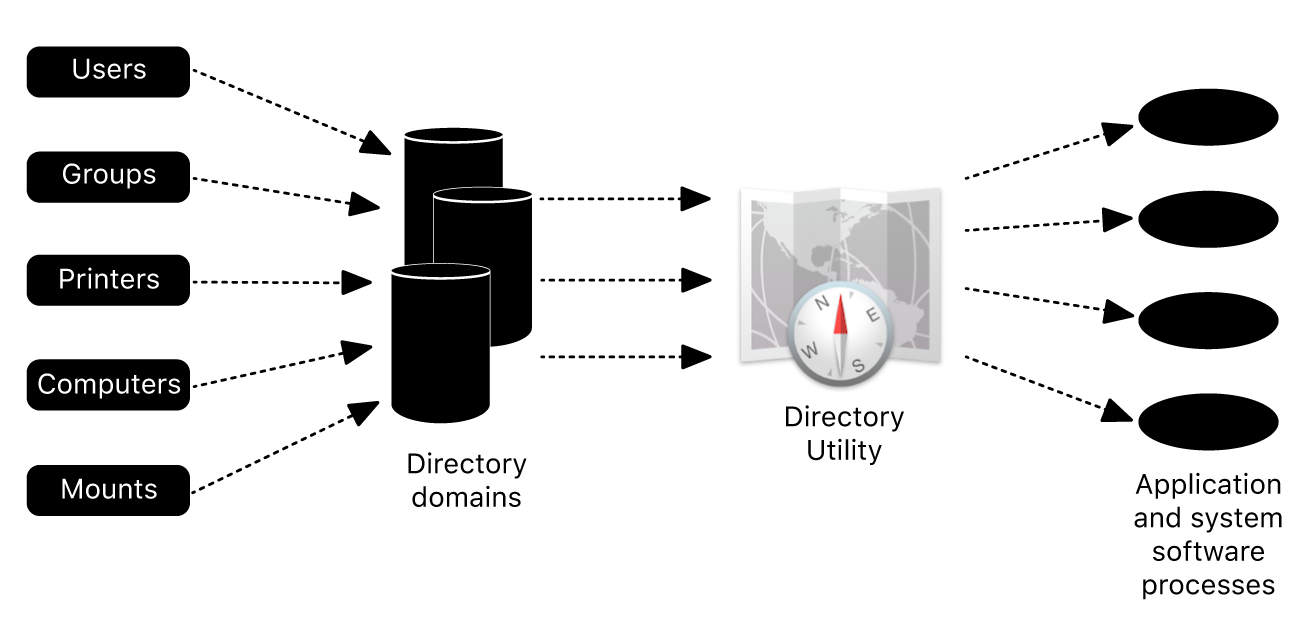
Note: macOS won’t be able to join an Active Directory domain without a domain functional level of at least Windows Server 2008, unless you explicitly enable “weak crypto.” Even if the domain functional levels of all domains are 2008 or later, the administrator may need to explicitly specify each domain trust to use Kerberos AES encryption.
How Mac uses DNS to query the Active Directory domain
macOS uses the Domain Name System (DNS) to query the topology of the on-premise Active Directory domain. It uses Kerberos for authentication and the Lightweight Directory Access Protocol (LDAPv3) for user and group resolution.
When macOS is fully integrated with Active Directory, users:
Are subject to the organization’s domain password policies
Use the same credentials to authenticate and gain authorization to secured resources
Can be issued user and machine certificate identities from an Active Directory Certificate Services server
Can automatically traverse a Distributed File System (DFS) namespace and mount the appropriate underlying Server Message Block (SMB) server.
For more information on connecting to a DFS without binding, see Distributed File System namespace support below.
You can also use the Directory payload in your mobile device management (MDM) solution to configure these settings, then push that payload to all of the Mac computers in your organization. For more information, see Directory MDM payload settings.
Mac clients assume full read access to attributes that are added to the directory. Therefore, it might be necessary to change the access control list (ACL) of those attributes to permit computer groups to read these added attributes.
Domain password policies
At bind time (and at periodic intervals thereafter), macOS queries the Active Directory domain for the password policies. These policies are enforced for all network and mobile accounts on a Mac.
During a login attempt while the network accounts are available, macOS queries Active Directory to determine the length of time before a password change is required. By default, if a password change is required within 14 days, the login window asks the user to change it. If the user changes the password, the change occurs in Active Directory as well as in the mobile account (if one is configured), and the login keychain password is updated. If the user dismisses the password request, the login window asks the user until the day before expiration. The user must change the password within 24 hours for login to proceed. A macOS administrator can change the default expiration notification for the login window from the command line by typing defaults write /Library/Preferences/com.apple.loginwindow PasswordExpirationDays -int <number of days>.
Note: macOS doesn’t support fine-grained password policies using Active Directory’s Password Settings Object (PSO). Only the default domain policy is used when calculating password expiration.
Distributed File System namespace support
macOS supports traversing distributed file system (DFS) namespaces if the Mac is bound to Active Directory. A Mac bound to Active Directory queries DNS and domain controllers in the Active Directory domain to automatically resolve the appropriate Server Message Block (SMB) server for a particular namespace.
You can use the Connect to Server feature in the Finder to specify the fully qualified domain name (FQDN) of the DFS namespace, which includes the DFS root to mount the network file system to. On a Mac, click the desktop to open the Finder, choose the Connect to Server command in the Go menu, then enter smb://resources.betterbag.com/DFSroot.
macOS uses any available Kerberos tickets and mounts the underlying Server Message Block (SMB) server and path. In some Active Directory configurations, you may need to populate the Search Domains field in the DNS configuration for the network interface with the fully qualified Active Directory domain name.
Tip: You can access and traverse DFS shares without binding to Active Directory if the DFS environment is configured to use fully qualified domain names in referrals. As long as the Mac can resolve the hostnames of the appropriate servers, connectivity succeeds without the Mac needing to be bound to the directory.
