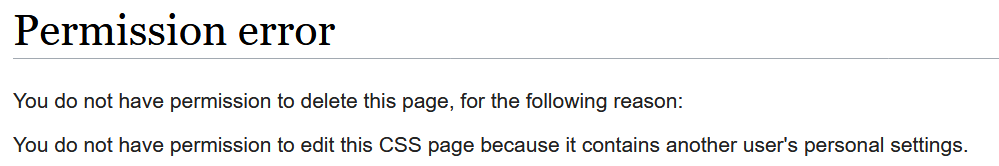
If you have delete, but not the right to edit such a page, you can't delete it.
This might be expected, but can lead into one problem: With the new group of people who can edit only these pages, they are only a few people who are a) admin and b) editor for css/js.
Means, if css or js gets abused to store abusive content or personal data, people are not able to delete.
Which means, that at least oversighter in all wikis need this right. Please take a look at this problem.