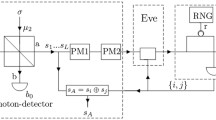
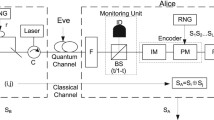
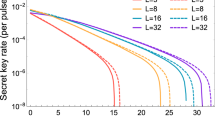
Abstract
As a promising quantum key distribution (QKD), most of the existing round-robin differential-phase-shift quantum key distribution (RRDPS-QKD) protocols have adopted the decoy-state method and have assumed the source states are exactly controlled. However, the precise manipulation of source states is impossible for any practical experiment, and the RRDPS-QKD with source errors has an unignorable impact on the performance of the protocol. In the paper, we study the four-intensity decoy-state RRDPS-QKD protocol with source errors, formulate the secure generation key rate of the proposed protocol, and do the numerical simulations to testify the deductions. The results show that our evaluation can estimate the influence of source errors.



Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.References
Lo, H.K., Chau, H.F.: Unconditional security of quantum key distribution over arbitrarily long distances. Science 283(5410), 2050 (1999)
Shor, P.W., Preskill, J.: Simple proof of security of the BB84 quantum key distribution protocol. Phys. Rev. Lett. 85(2), 441 (2000)
Mayers, D.: Unconditional security in quantum cryptography. J. ACM 48(3), 351 (2001)
Bennett, C.H., Brassard, G.: Quantum cryptography: public key distribution and coin tossing. Theor. Comput. Sci. 560, 7 (2014)
Lo, H.K., Ma, X., Chen, K.: Decoy state quantum key distribution. Phys. Rev. Lett. 94(23), 230504 (2005)
Wang, X.B.: Beating the photon-number-splitting attack in practical quantum cryptography. Phys. Rev. Lett. 94(23), 230503 (2005)
Wang, X.B., Yang, L., Peng, C.Z., Pan, J.W.: Decoy-state quantum key distribution with both source errors and statistical fluctuations. New J. Phys. 11(7), 075006 (2009)
Chi, H.H., Yu, Z.W., Wang, X.B.: Decoy-state method of quantum key distribution with both source errors and statistics fluctuations. Phys. Rev. A 86, 4 (2012)
Lo, H.K., Curty, M., Qi, B.: Measurement-device-independent quantum key distribution. Phys. Rev. Lett. 108(13), 130503 (2012)
Yin, H.L., Chen, T.Y., Yu, Z.W., Liu, H., You, L.X., Zhou, Y.H., Chen, S.J., Mao, Y., Huang, M.Q., Zhang, W.J., Chen, H., Li, M.J., Nolan, D., Zhou, F., Jiang, X., Wang, Z., Zhang, Q., Wang, X.B., Pan, J.W.: Measurement-device-independent quantum key distribution over a 404 km optical fiber. Phys. Rev. Lett. 117(19), 190501 (2016)
Gisin, N., Ribordy, G.G., Tittel, W., Zbinden, H.: Quantum cryptography. Rev. Mod. Phys. 74(1), 145 (2002)
Gottesman, D., Lo, H.K., Lutkenhaus, N., Preskill, J.: Security of quantum key distribution with imperfect devices. Quantum. Inf. Comput 4(5), 325 (2004)
Sasaki, T., Yamamoto, Y., Koashi, M.: Practical quantum key distribution protocol without monitoring signal disturbance. Nature 509(7501), 475 (2014)
Mizutani, A., Imoto, N., Tamaki, K.: Robustness of the round-robin differential-phase-shift quantum-key-distribution protocol against source flaws. Phys. Rev. A 92(6), 060303 (2015)
Zhang, Z., Yuan, X., Cao, Z., Ma, X.: Practical round-robin differential-phase-shift quantum key distribution. New J. Phys. 19, 033013 (2017)
Sasaki, T., Koashi, M.: A security proof of the round-robin differential phase shift quantum key distribution protocol based on the signal disturbance. Quantum.Sci. Technol 2(2), 024006 (2017)
Yin, Z.Q., Wang, S., Chen, W., Han, Y.G., Wang, R., Guo, G.C., Han, Z.F.: Improved security bound for the round-robin-differential-phase-shift quantum key distribution. Nat. Commun. 9, 457 (2018)
Zhang, Y.Y., Bao, W.S., Zhou, C., Li, H.W., Wang, Y., Jiang, M.S.: Practical round-robin differential phase-shift quantum key distribution. Opt. Express 24(18), 20763 (2016)
Wang, L., Zhao, S.: Round-robin differential-phase-shift quantum key distribution with heralded pair-coherent sources. Quantum Inf. Process. 16(4), 100 (2017)
Liu, L., Guo, F.Z., Qin, S.J., Wen, Q.Y.: Round-robin differential-phase-shift quantum key distribution with a passive decoy state method. Sci. Rep. 7, 42261 (2017)
Hu, K., Mao, Q.P., Zhao, S.M.: Round robin differential phase shift quantum key distribution using heralded single photon source and detector decoy. Acta Opt. Sin. 37(05), 0527002 (2017)
Mao, Q.P., Wang, L., Zhao, S.M.: Plug-and-play round-robin differential phase-shift quantum key distribution. Sci. Rep. 7(1), 15435 (2017)
Wang, X.B., Peng, C.Z., Zhang, J., Yang, L., Pan, J.W.: General theory of decoy-state quantum cryptography with source errors. Phys. Rev. A 77(4), 042311 (2008)
Wang, Q., Wang, X.B.: Simulating of the measurement-device independent quantum key distribution with phase randomized general sources. Sci. Rep. 4, 4612 (2014)
Jiang, C., Yu, Z.W., Wang, X.B.: Measurement-device-independent quantum key distribution with source state errors in photon number space. Phys. Rev. A 94(6), 062323 (2016)
Wang, S., Zhang, S.L., Li, H.W., Yin, Z.Q., Zhao, Y.B., Chen, W., Han, Z.F., Guo, G.C.: Decoy-state theory for the heralded single-photon source with intensity fluctuations. Phys. Rev. A 79(6), 062309 (2009)
Zhou, C., Bao, W.S., Fu, X.Q.: Decoy-state quantum key distribution for the heralded pair coherent state photon source with intensity fluctuations. Sci. China Inf Sci. 53(12), 2485 (2010)
Gobby, C., Yuan, Z.L., Shields, A.J.: Quantum key distribution over 122 km of standard telecom fiber. Appl. Phys. Lett. 84(19), 3762 (2004)
Acknowledgements
The paper is supported by the National Natural Science Foundation of China (Grant Nos. 61871234, 61475075, 11847062) and the Postgraduate Research & Practice Innovation Program of Jiangsu Province (Grant No. KYLX15-0832).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
The paper is supported by the National Natural Science Foundation of China (Grant Nos. 61871234, 61475075, 11847062) and the Postgraduate Research & Practice Innovation Program of Jiangsu Province (Grant No. KYLX15-0832)
Appendix
Appendix
In this section, we will give the lower bounds of \(D_0\), \(D_1\), \(D_2\).
In order to get the lower bound of \(D_0\), applying \(p_{1,\nu _1 }^L\) Eq. (9) \(-p_{1,\nu _2 }^U\) Eq. (8), we have
According to the definitions of \(D_0\), \(D_1\) and \(D_2\), we get
Due to the conditions of Eq.(15), we can obtain an inequality \(p_{1,\nu _1 }^L p_{k,\nu _2 }^U - p_{1,\nu _2 }^U p_{k,\nu _1 }^L \le 0 \quad for\;all\;k \ge 2\). Therefore, the inequality in Eq.(22) becomes
and the lower bound of \(D_0\) is obtained by
Then, similar to Eq.(21), by \(p_{0,\nu _2 }^L\) Eq. (8) \(-p_{0,\nu _1 }^U\) Eq. (9), we have
Here, the inequality that \(\frac{(p_{0,\nu _2 }^L p_{k,\nu _1 }^U - p_{0,\nu _1 }^U p_{k,\nu _2 }^L )}{{p_{k,\mu }^L }} \le \frac{(p_{0,\nu _2 }^L p_{2,\nu _1 }^U - p_{0,\nu _1 }^U p_{2,\nu _2 }^L )}{{p_{2,\mu }^L }}\) for \(k \ge 2\) is adopted to prove the inequality in Eq.(25). Consequently, the lower bound of \(D_1\) can be estimated by
where \(D_0^L\) has been calculated in Eq.(24).
Combining the two equations [\(p_{0,\nu _2}^L\) Eq. (8)\(-p_{0,\nu _1}^U\) Eq. (9) ] and [\(p_{0,\nu _3}^U\) Eq. (9)\(-p_{0,\nu _2 }^L\) Eq. (10)], we can have
where the inequality is due to \(\frac{{(p_{0,\nu _2 }^L p_{k,\nu _1 }^U - p_{0,\nu _1 }^U p_{k,\nu _2 }^L )(p_{0,\nu _3 }^U p_{1,\nu _2 }^L - p_{0,\nu _2 }^L p_{1,\nu _3 }^U ) - (p_{0,\nu _3 }^U p_{k,\nu _2 }^L - p_{0,\nu _2 }^L p_{k,\nu _3 }^U )(p_{0,\nu _2 }^L p_{1,\nu _1 }^U - p_{0,\nu _1 }^U p_{1,\nu _2 }^L )}}{{p_{k,\mu }^L }} \le \frac{{(p_{0,\nu _2 }^L p_{3,\nu _1 }^U - p_{0,\nu _1 }^U p_{3,\nu _2 }^L )(p_{0,\nu _3 }^U p_{1,\nu _2 }^L - p_{0,\nu _2 }^L p_{1,\nu _3 }^U ) - (p_{0,\nu _3 }^U p_{3,\nu _2 }^L - p_{0,\nu _2 }^L p_{3,\nu _3 }^U )(p_{0,\nu _2 }^L p_{1,\nu _1 }^U - p_{0,\nu _1 }^U p_{1,\nu _2 }^L )}}{{p_{3,\mu }^L }} \) for \(k\ge 3\).
Hence, the lower bound of \(D_2\) can be expressed by
Rights and permissions
About this article
Cite this article
Mao, QP., Wang, L. & Zhao, SM. Decoy-state round-robin differential-phase-shift quantum key distribution with source errors. Quantum Inf Process 19, 56 (2020). https://doi.org/10.1007/s11128-019-2552-7
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11128-019-2552-7