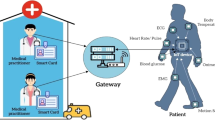
Abstract
The convergence with the emerging digital twin technology has been envisaged as the looming of a smart cloud-based healthcare system. Precision clone simulation of the patients and medical service builds a bridge to the virtual medical world, enabling diagnosing, monitoring, and future prediction to offer enhanced medical services. Cloud services provider plays a crucial role in endowing a way to interlink the physical world to the virtual medical world through outsourced storage, a communication platform, reduced computational cost, and the relevance of hosting and other services over the internet offered by it. However, any alteration, deviation, or amendment of the physical patient’s and its digital twin’s stored data in the cloud storage has been one of the security liabilities. In this work, we propose a blockchain-assisted certificateless public auditing mechanism for the cloud-based digital twin healthcare networks to substantiate the data integrity in cloud storage. Blockchain in the proposed mechanism enables keeping the auditing process and outsourcing activities log. Meanwhile, it also enjoys the benefits of batch auditing and pairing-free operations. The proposed work is demonstrated to be provably secure and efficient in achieving security goals like storage correctness, privacy-preserving, and public verifiability. Furthermore, the computational overhead of the presented work is shown to be efficient with contrasted with some existing works.







Similar content being viewed by others
Data availability
The authors affirm that the data supporting the study finding are included in the paper.
References
Son, Seunghwan, Kwon, Deokkyu, Lee, Joonyoung, Sungjin, Yu., Jho, Nam-Su., Park, Youngho: On the design of a privacy-preserving communication scheme for cloud-based digital twin environments using blockchain. IEEE Access 10, 75365–75375 (2022)
Wang, Cong, Wang, Qian, Ren, Kui, Cao, Ning, Lou, Wenjing: Toward secure and dependable storage services in cloud computing. IEEE Trans. Services Comput. 5(2), 220–232 (2011)
Wang, Cong, Wang, Qian, Ren, Kui, Lou Wenjing: Privacy-preserving public auditing for data storage security in cloud computing. In 2010 proceedings ieee infocom, pages 1–9. Ieee, (2010)
Grieves, Michael, Vickers, John: Digital twin: Mitigating unpredictable, undesirable emergent behavior in complex systems. In: Transdisciplinary Perspectives Complex Sys., pp. 85–113. Springer, Cham (2017)
Glaessgen, Edward, Stargel, David: The digital twin paradigm for future nasa and us air force vehicles. In 53rd AIAA/ASME/ASCE/AHS/ASC structures, structural dynamics and materials conference 20th AIAA/ASME/AHS adaptive structures conference 14th AIAA, page 1818, (2012)
Kazi Masudul Alam and Abdulmotaleb El Saddik: C2ps: A digital twin architecture reference model for the cloud-based cyber-physical systems. IEEE Access 5, 2050–2062 (2017)
Liu, Ying, Zhang, Lin, Yang, Yuan, Zhou, Longfei, Ren, Lei, Wang, Fei, Liu, Rong, Pang, Zhibo, Jamal Deen, M.: A novel cloud-based framework for the elderly healthcare services using digital twin. IEEE Access 7, 49088–49101 (2019)
Wang, Chenyu, Cai, Zhipeng, Li, Yingshu: Sustainable blockchain-based digital twin management architecture for iot devices. IEEE Internet Things J. 10(8), 6535–6548 (2022)
Huang, Sihan, Wang, Guoxin, Yan, Yan, Fang, Xiongbing: Blockchain-based data management for digital twin of product. J. Manuf. Syst. 54, 361–371 (2020)
Ateniese, Giuseppe, Di Pietro, Roberto, Mancini, Luigi V, Tsudik, Gene: Scalable and efficient provable data possession. In Proceedings of the 4th international conference on Security and privacy in communication netowrks, pages 1–10, (2008)
Ateniese, Giuseppe, Burns, Randal, Curtmola, Reza, Herring, Joseph, Kissner, Lea, Peterson, Zachary, Song, Dawn: Provable data possession at untrusted stores. In Proceedings of the 14th ACM conference on Computer and communications security, pages 598–609, (2007)
Juels, Ari, Kaliski Jr. Pors, Burton S: Proofs of retrievability for large files. In Proceedings of the 14th ACM conference on Computer and communications security, pages 584–597, (2007)
Shacham, Hovav, Waters, Brent: Compact proofs of retrievability. In International conference on the theory and application of cryptology and information security, pages 90–107. Springer, (2008)
Bowers, Kevin D, Juels, Ari, Oprea, Alina: Hail: A high-availability and integrity layer for cloud storage. In Proceedings of the 16th ACM conference on Computer and communications security, pages 187–198, (2009)
Zargad, Snehal Vilas, Tambile, Amruta Vijay, Sankoli, Shivangi Shashikant, Bhongale, Rajashree Chandrakant: Data integrity checking protocol with data dynamics and public verifiability for secure cloud computing. Int. J. Comput. Sci. Inf. Technol. (IJCSIT) 5(3), 4062–4064 (2014)
Wang, Cong: Chow, Sherman SM, Wang, Qian, Ren, Kui, Lou, Wenjing: Privacy-preserving public auditing for secure cloud storage. IEEE Trans. Comput. 62(2), 362–375 (2011)
Shamir, Adi: Identity-based cryptosystems and signature schemes. In Workshop on the theory and application of cryptographic techniques, pages 47–53. Springer, (1984)
Huang, Kun, Xian, Ming, Shaojing, Fu., Liu, Jian: Securing the cloud storage audit service: defending against frame and collude attacks of third party auditor. IET Commun. 8(12), 2106–2113 (2014)
Kang, Baoyuan, Xu, Danhui: Secure electronic cash scheme with anonymity revocation. Mobile Information Systems, 2016, (2016)
Wang, Huaqun, Qianhong, Wu., Qin, Bo., Domingo-Ferrer, Josep: Identity-based remote data possession checking in public clouds. IET Inf. Secur. 8(2), 114–121 (2014)
Zhang, Jianhong, Dong, Qiaocui: Efficient id-based public auditing for the outsourced data in cloud storage. Inf. Sci. 343, 1–14 (2016)
Yu, Yong: Xue, Liang, Au, Man Ho, Susilo, Willy, Ni, Jianbing, Zhang, Yafang, Vasilakos, Athanasios V, Shen, Jian: Cloud data integrity checking with an identity-based auditing mechanism from rsa. Futur. Gener. Comput. Syst. 62, 85–91 (2016)
Al-Riyami, Sattam S, Paterson, Kenneth G: Certificateless public key cryptography. In International conference on the theory and application of cryptology and information security, pages 452–473. Springer, (2003)
He, Debiao, Padhye, Sahadeo, Chen, Jianhua: An efficient certificateless two-party authenticated key agreement protocol. Comput. Math. Appl. 64(6), 1914–1926 (2012)
He, Debiao, Chen, Jianhua, Jin, Hu.: A pairing-free certificateless authenticated key agreement protocol. Int. J. Commun. Syst. 25(2), 221–230 (2012)
He, Debiao, Chen, Yitao, Chen, Jianhua: An efficient certificateless proxy signature scheme without pairing. Math. Comput. Model. 57(9–10), 2510–2518 (2013)
Liu, Jingwei, Zhang, Zonghua, Chen, Xiaofeng, Kwak, Kyung Sup: Certificateless remote anonymous authentication schemes for wirelessbody area networks. IEEE Trans. Parallel Distrib. Sys. 25(2), 332–342 (2013)
Zhao, Zhenguo: An efficient anonymous authentication scheme for wireless body area networks using elliptic curve cryptosystem. J. Med. Syst. 38(2), 1–7 (2014)
Wang, Boyang, Li, Baochun, Li, Hui, Li, Fenghua (2013) Certificateless public auditing for data integrity in the cloud. In 2013 IEEE conference on communications and network security (CNS) p. 136–144 IEEE
He, Debiao, Zeadally, Sherali, Libing, Wu.: Certificateless public auditing scheme for cloud-assisted wireless body area networks. IEEE Syst. J. 12(1), 64–73 (2015)
Kang, Baoyuan, Wang, Jiaqiang, Shao, Dongyang: Certificateless public auditing with privacy preserving for cloud-assisted wireless body area networks. Mobile Inform. Sys. (2017). https://doi.org/10.1155/2017/2925465
Yan, Hao, Li, Jiguo, Han, Jinguang, Zhang, Yichen: A novel efficient remote data possession checking protocol in cloud storage. IEEE Trans. Inf. Forensics Secur. 12(1), 78–88 (2016)
Shen, Jian, Shen, Jun, Chen, Xiaofeng, Huang, Xinyi, Susilo, Willy: An efficient public auditing protocol with novel dynamic structure for cloud data. IEEE Trans. Inf. Forensics Secur. 12(10), 2402–2415 (2017)
Li, Xiong, Liu, Shanpeng, Rongxing, Lu.: Comments on “a public auditing protocol with novel dynamic structure for cloud data’’. IEEE Trans. Inf. Forensics Secur. 15, 2881–2883 (2020)
Li, Xiong, Liu, Shanpeng, Lu, Rongxing, Khan, Muhammad Khurram, Ke, Gu., Zhang, Xiaosong: An efficient privacy-preserving public auditing protocol for cloud-based medical storage system. IEEE J. Biomed. Health Inform. 26(5), 2020–2031 (2022)
Nakamoto, Satoshi 2008 Bitcoin: a peer-to-peer electronic cash system. Decentralized Business Review, p 21260,
Yang, Xu., Zhang, Cheng, Wang, Guojun, Qin, Zheng, Zeng, Quanrun: A blockchain-enabled deduplicatable data auditing mechanism for network storage services. IEEE Trans. Emerg. Top. Comput. 9(3), 1421–1432 (2020)
Yuan, Haoran, Chen, Xiaofeng, Wang, Jianfeng, Yuan, Jiaming, Yan, Hongyang, Susilo, Willy: Blockchain-based public auditing and secure deduplication with fair arbitration. Inf. Sci. 541, 409–425 (2020)
Zhang, Yuan, Chunxiang, Xu., Lin, Xiaodong, Shen, Xuemin: Blockchain-based public integrity verification for cloud storage against procrastinating auditors. IEEE Trans. Cloud Comput. 9(3), 923–937 (2019)
Zhao, Jie, Huang, Hejiao, Gu, Chonglin, Hua, Zhongyun, Zhang, Xiaojun: Blockchain-assisted conditional anonymity privacy-preserving public auditing scheme with reward mechanism. IEEE Sys. J. 16(3), 447–4488 (2021)
Ming, Yang, Cheng, Hongliang: Efficient certificateless conditional privacy-preserving authentication scheme in vanets. Mobile Inform. Sys. (2019). https://doi.org/10.1155/2019/7593138
Xiang, Dengmei, Li, Xuelian, Gao, Juntao, Zhang, Xiachuan: A secure and efficient certificateless signature scheme for internet of things. Ad Hoc Netw. 124, 102702 (2022)
Funding
Not applicable.
Author information
Authors and Affiliations
Contributions
Deepika: Conceptual and writing the manuscript. PK: Review, Supervision, Conceptual and writing the manuscript. SP: Review and Implementation of the algorithm.
Corresponding author
Ethics declarations
Conflict of interest
The author declare no conflict of interest, financial or otherwise.
Ethics approval
Not applicable.
Consent to participate
Yes.
Consent for publication
Yes.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Kumari, D., Kumar, P. & Prajapat, S. A blockchain assisted public auditing scheme for cloud-based digital twin healthcare services. Cluster Comput 27, 2593–2609 (2024). https://doi.org/10.1007/s10586-023-04101-y
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10586-023-04101-y